Is BlueJay Video Visit HIPAA compliant?
BlueJay’s Video Visit platform helps you to be HIPAA compliant in two ways :
- It protects data privacy in that all audio/video communication is securely encrypted and transmitted from point-to-point such that even BlueJay Health does not have access to any identifiable health information that may be communicated.
- BlueJay Health offers the HIPAA-required Business Associate Agreement where BlueJay Health agrees to be responsible for keeping all patient information secure and to immediately report any breach of personal health information.
You can learn more about HIPAA in the sections below:
HIPAA and Health IT
HIPAA is a federal law that protects the privacy of your personal health information. At the same time it allows health care providers and certain related operations enough access to the information they need to do their jobs effectively. HIPAA includes several rules and provisions that set guidelines and requirements for the administration and enforcement of HIPAA. The relevant ones for the implementation of health information technology and the exchange of protected health information in an electronic environment are the Privacy Rule and the Security Rule , as well as the HITECH Act which further enforced the two in 2009.
*State laws may have more stringent requirements than federal laws, however, in cases of conflict, federal law supersedes state law.
Highlights Of The Privacy Rule, The Security Rule, and the HITECH Act
- The Privacy Rule, applies to protected health information (PHI) in any form whether paper, oral, electronic, etc. While it requires covered entities to put in place "administrative, physical, and technical safeguards" for protecting PHI, it differs from the Security Rule in that it discusses the cases in which PHI can be used, when authorization is required and what are patients' rights with respect to their health information. (Page 8335 of the final Security Rule)
Summary of Privacy Rule -
Security Rule Guidance Material : The US Department of Health & Human Services (HHS) now also offers a Security Risk Assessment (SRA) tool : To help organizations ensure they are compliant with HIPAA’s administrative, technical, and physical safeguards and to expose areas where their PHI may be at risk
The figure below gives you an idea of the security measures covered by the Security Rule. (from paper "Reassessing Your Security Practices in a Health IT Environment: A Guide for Small Health Care Practices")
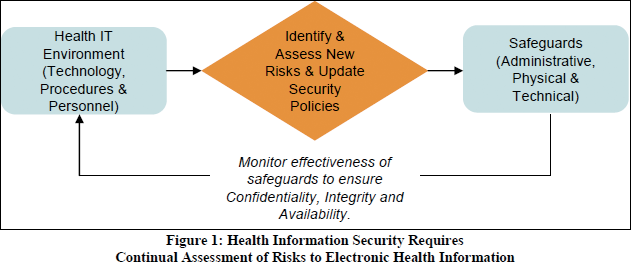
- The HITECH Act essentially added teeth to the HIPAA Privacy and Security Rules by specifying levels of violations and penalties for violations. It also requires periodic audits to ensure that covered entities and business associates are complying with the HIPAA Privacy and Security Rules and Breach Notification. HITECH modifications to privacy and security
Not all operations that handle health-related information must follow HIPAA law (such as many schools, state agencies, law enforcement agencies, or municipal offices). Under HIPAA the 2 groups that must follow HIPAA rules are
- Covered entities - health care providers, health plans, and health clearinghouses /
- Business associates - a person or group providing certain functions or services for a covered entity which require access to identifiable health information, such as a CPA firm, an attorney, or an independent medical transcriptionist; More business associate FAQs here<>
BlueJay Health would be considered the business associate of a covered entity that uses Video Visit to communicating private health information with a client.
How is HIPAA involved in your use of video visit?
BlueJay’s Video Visit may involve the electronic exchange of health information which is protected under HIPAA law. Security considerations with Video Visit may involve making sure unauthorized third parties cannot to record or "listen in" on a Video Visit session. Other video collaboration features affecting security may include text chat, and file-transfer.
Video visit would only be one small piece to consider when establishing and maintaining HIPAA-compliant IT security standards as described by the Privacy Rule and the Security Rule.
How does BlueJay Health allow you to comply with the HIPAA Privacy and Security Rules?
BlueJay Health has several characteristics that make it easy to protect the confidentiality of protected health information:
- Peer-to-Peer sessions
BlueJay Health uses a managed peer-to-peer architecture, where video (and other media) are streamed directly from endpoint to endpoint. Information is never stored on any BlueJay Health servers or intercepted by BlueJay Health in any way. - Encryption
All media traffic is encrypted no matter the endpoint you use (web or mobile) or the session setup you choose. That means that you are safe when using BlueJay Video Visit even if use it in an open public hotspot. BlueJay Video Visit service uses the AES cipher with 128-bit keys to encrypt audio and video, and HMAC-SHA1 to verify data integrity.
Is BlueJay Health certified for use under HIPAA?
Certification of health technology is regulated under the HITECH Act by the Office of the National Coordinator for Health Information Technology ( ONC) in collaboration with the National Institute of Standards and Technology ( NIST). HIPAA rules do "not assume the task of certifying software and off-the-shelf products" (p. 8352 of the Final Security Rule) neither do they set criteria for or accredit independent agencies that do HIPAA certifications. In short, this means that the third-party HIPAA certification groups you may use are not regulated by any federal accreditation agency.
Currently HITECH only provides for the testing and certification of Electronic Health Records (EHR) programs and modules. The certification is generally used to qualify health operations for Medicare and Medicaid EHR Incentive Programs.
Does data have to be encrypted to be HIPAA compliant?
The Security Rule does not require encryption if an entity can prove it is not reasonable or appropriate to do so. However, it is a good idea to encrypt data whenever possible because in the case that there is a data breach, proper encryption exempts HIPAA-covered entities from the Breach Rule (section 13402 of the HITECH Act), which requires notification of PHI that has not been secured (i.e. encrypted) according to the security guidance publication (74 FR 19006 on April 27, 2009):
"While covered entities and business associates are not required to follow the guidance, the specified technologies and methodologies, if used, create the functional equivalent of a safe harbor, and thus, result in covered entities and business associates not being required to provide the notification otherwise required by section 13402 in the event of a breach." (p. 19008)
Encryption processes that have been tested and meet the guidance standard:
(i) "Valid encryption processes for data at rest are consistent with NIST Special Publication 800–111, Guide to Storage Encryption Technologies for End User Devices." (p. 19009-10)
(ii) "Valid encryption processes for data in motion are those that comply with the requirements of Federal Information Processing Standards (FIPS) 140–2. These include, as appropriate, standards described in NIST Special Publications 800–52, Guidelines for the Selection and Use of Transport Layer Security (TLS) Implementations; 800–77, Guide to IPsec VPNs; or 800–113, Guide to SSL VPNs, and may include others which are FIPS 140–2 validated." (p. 19009-10)
Official Documentation For HIPAA
-
HIPAA - Health Insurance Portability and Accountability Act of 1996, Public Law 104-191, the complete suite of HIPAA Administrative Simplification Regulations can be found at 45 C.F.R. Part 160, Part 162, and Part 164
-
The Privacy Rule - "Standards for Privacy of Individually Identifiable Health Information" and is found at 45 CFR Part 160 and Subparts A and E of Part 164.
-
The Security Rule - "Security Standards for the Protection of Electronic Protected Health Information" and is found at 45 CFR Part 160 and Subparts A and C of Part 164.
-
HITECH - Health Information Technology for Economic and Clinical Health Act
-
Modifications to the HIPAA Privacy, Security, Enforcement, and Breach Notification Rules - 45 C.F.R. Parts 160 and 164






